The biggest difference between Windows 10 and Windows 11 is that with Windows 10, one could turn off UEFI and Secure Boot to replace Windows with Linux. With Windows 11, both UEFI and Secure Boot are required. In this article, we will outline the drawbacks of Secure Boot and UEFI – which are so great that if you have the misfortune of having purchased a Windows 11 computer, your only option is to throw it in the dumpster.
What is UEFI BIOS?
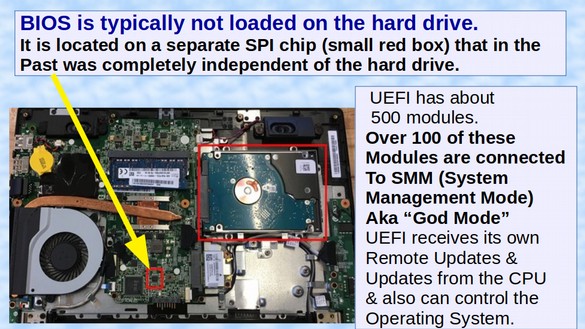
For more than 20 years, BIOS consisted of a small program that was independent of the operating system. Then, in May 2006, Bill Gates gave a speech announcing a “better” replacement for BIOS called the Unified Extensible Firmware Interface (aka UEFI) – a secret closed source program that was 10 times bigger than the prior BIOS.
UEFI is now a near monopoly BIOS found on all Windows and Apple computers and nearly all Linux computers. Thankfully, in 2007, Google began supporting Coreboot - a free open source alternative to UEFI. Coreboot eventually became the BIOS program for all Chromebooks. Recently, a Linux computer maker called Purism also started using Coreboot BIOS on their Librem 14 Laptops.
Is UEFI BIOS Secure?
We know from the Snowden and Vault 7 documents that the NSA has several back doors into the Windows Operating System since at least 1998. Here, we will look at evidence that the NSA has placed back doors in the UEFI BIOS firmware program since 2007.
Why is a Secure BIOS Important?
If a hacker takes over your BIOS, they can control your operating system, applications and all of your documents stored on your computer hard drive.
Dark History of UEFI
The UEFI security signing mechanism is identical to the Microsoft Windows security signing. I do not mean similar. I mean IDENTICAL. Many sections of UEFI code even begins with the word “win.” Here is a quote from Bill on May 23, 2006, the day he announced UEFI:

https://news.microsoft.com/speeches/bill-gates-winhec-2006/
UEFI version 1.0 in 2006 was not that different from BIOS. In particular, it did not include secure boot. Neither did UEFI version 2.1 which was released on January 7, 2007. So what was Bill Gates talking about in his 2006 speech when he referred to a “new capability”? Could it be that Bill knew something completely different was in the works? Little did we know then that by “us” Bill was referring to his Prism Partners at the NSA and that by “new capability” Bill meant that the NSA would soon be able to hack into any computer on the planet by hacking into the new back doors they placed in the UEFI BIOS.
Beginning in 2008, just a few months after Microsoft joined the NSA PRISM program, strange things began to happen. The biggest change was with UEFI version 2.2. The purpose began to change, the tools began to change and even the code began to change. Suddenly, instead of being merely an update to BIOS, UEFI became a nuclear weapon with the addition of Secure Boot. At the same time, the UEFI manual grew to be nearly 2,200 pages. Who could have done that? Pay no attention to that man behind the curtain (who also happens to be the richest man in the world).
Then UEFI version 2.3 was released in April 2011 – just 6 months before the “developer” release of Windows 8 in September 2011. Here is a partial diagram of the UEFI Structure.
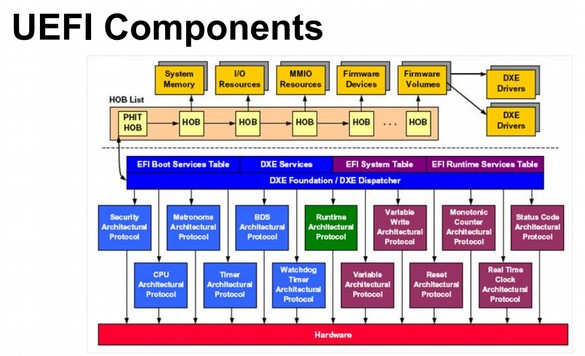
In 2007 to 2008, Microsoft and their Prism Partners, turned UEFI from a simple, harmless hardware initializer into a security nightmare.
Nine Design Flaws of UEFI
First, UEFI was and developed in secrecy. As security experts have often pointed out, secrecy means a lack of feedback and is therefore a model for failure. Incredibly, there is no way to know what is in the UEFI program because all members of the UEFI forum must sign an oath of secrecy.
This is the exact opposite of how the open source community works – where everyone knows about all bug reports and everyone works together and shares ideas and solutions to fix the bugs.
Second, UEFI is an enormous program with over 7000 files and nearly 100 MB of code. There is safety in simplicity. More code simply leads to more ways to attack the system.
Third, UEFI has 'call home” feedback loops which were not present on BIOS and are not present on Core Boot. This is perhaps the worst shortcoming of UEFI.
BIOS and Core Boot are completely separate from the operating system. Therefore attacks on the operating system rarely if ever affect the start up program. However, because secure boot will not work without a “call home” open back door, UEFI is the first start up program to ever have a call home feedback loop. This feedback loop would make it possible for an attacker who gains access to the Authorized Certificates to rewrite the code on the start up chip.
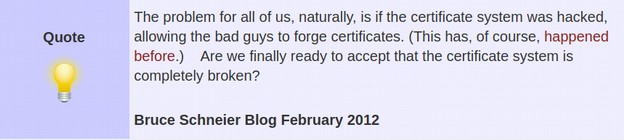
Fourth, the Secure Boot Certificate method has already been shown to be open to attack. Security expert, Bruce Schneier calls the certificate system “completely broken.”
Fifth, UEFI uses Microsoft programming languages which use backward slashes for file names. Backward slashes have previously led to easy attacks to the Windows operating system – this same attacks could go directly to the Start up chip due to the “call home” open back doors in UEFI.
Sixth, Secure boot is not secure
Secure boot uses a combination of keys to prevent you from downloading any program Microsoft feels they do not like. The problem is that some of the keys are public and the rest have been hacked in the past – and will be hacked again in the future. So the only one blocked from installing programs to your computer by secure boot is you. Microsoft has left the back door to your computer open since 1997. With Secure Boot, they have now also left the front door to your computer open. Secure Boot opens up the Startup program to attack because it uses the same top down easily copied digital image system the Microsoft Windows uses to protect its open back door. The name Secure Boot lulls users into a false sense of security that their computer is secure when it is not.
Seventh, with Windows 11, Secure Boot can not longer be disabled
Hackers now know that all they need to do is get past Secure Boot and they can remotely control your computer.
Eighth, claims that there are advantages to UEFI are false
We have been subjected to a wave of propaganda trying to convince us that UEFI has some kind of benefit. For example, they claim that UEFI can handle partitions bigger than 2 Terabytes. Well, so can Core Boot. Even the old BIOS can as long as they are divided between partitions. You will also hear that UEFI allows you to have a much larger number of partitions. This is also not true. Core Boot has the same partitioning ability as UEFI and even the old BIOS system will let you have as many partitions as you want.
You will also be told that Secure Boot protects against Root Kit infections. It does not. Anyone capable of creating a root kit attack is also capable of creating fake keys similar to the process used by the Flame virus. So do not be fooled. The only purpose of UEFI is to maintain and expand the Microsoft monopoly. If you want your system to be safe and under your control, then install and use Linux. and/or you need to get a computer with Core Boot.
Ninth, you can not get rid of UEFI
Unfortunately, it is quite difficult to replace UEFI with Core Boot because UEFI is not on your hard drive. The only way you can get rid of UEFI is to return the computer to the store where you bought it, demand a refund and buy a computer with Core Boot on it. It is also not likely that Windows will work on anything other than UEFI because UEFI and Windows were basically made for each other.
The Problem with a UEFI BIOS Monopoly
In June 2013, Edward Snowden provided a million NSA documents to reporters. Some of these Documents referred to the “Prism Partners Program” that the NSA began with Microsoft, Intel and others in 2007.

Another Snowden document, published by Der Spiegel in 2015, was a July 11, 2006 NSA “Persistence Division” job announcement looking for programmers to develop EFI firmware hacking tools beginning in January 2007: “BERSERKR is a persistent backdoor that is implanted into the BIOS and runs from SMM…

The firmware implant hides from the user on a hidden Partition that cannot be seen or accessed by the user but which can be activated by a secret “hook” or custom command. http://www.spiegel.de/media/media-35661.pdf
The following image is from a 2007 NSA Slideshow supplied by Snowden and made public by the Intercept on January 24 2019. The NSA and its Sub-contractors have at least 100,000 hackers. Many of these are in TAO or Tailored Access Operations. TAO has 6 Divisions. One of these Divisions is called “Access Tech & Operations.”
https://theintercept.com/document/2019/01/24/tailored-access-operations-2007/
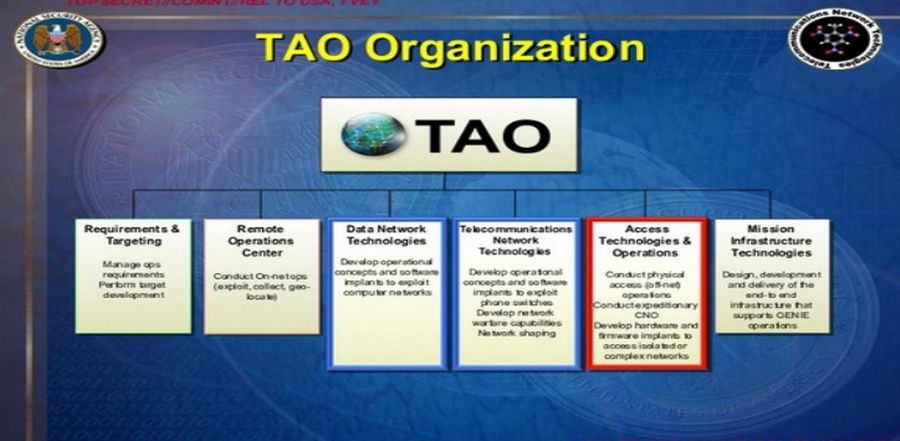
This is slide 7 which describes the mission of the Persistence Division which is part of the Access Tech Division. Note the emphasis on remote access to Firmware and working with their “community partners” aka Microsoft and Intel.

NSA Persistence Division + MS + INTEL = UEFI
Another January 2007 NSA document referred to Supply Chain attacks using “Sierra Mist” which is a hidden partition on nearly all hard drives used to compromise “Firmware BIOS”. The code is for Windows OS and is written in C++.

Recall that in 2007 Microsoft and Intel created more than 500 UEFI modules including more than 100 Modules connected to the Intel SMM (System Management Mode). This is clear evidence that Microsoft and Intel were working directly with the NSA in 2007 to create UEFI as “a new mechanism to achieve persistence.”
The Difference Between a Computer Virus and an APT Rootkit
Most computer users tend to worry about their computer picking up viruses or hacking programs when they go online. Users add “anti-virus” software to their computers to help protect against these viruses. Operating system “updates” are also used to protect against viruses. However, since 2007, thanks to cyber weapons created by the NSA, computers are now subjected to much more harmful attacks – attacks that can take over or wipe out your entire computer.
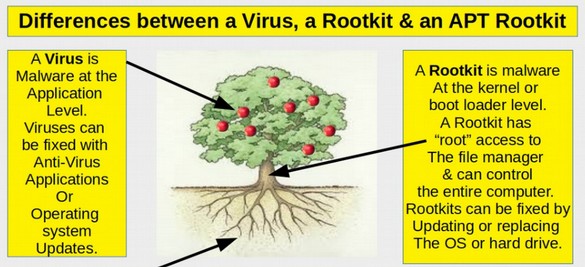
These new attacks are all Advanced Persistent Threat or APT attacks. An Advanced Persistent Threat Rootkit is malware hidden in the BIOS (UEFI). APT Rootkits can survive cleaning, updating or replacing the hard drive or the kernel or the operating system.
History of UEFI Advanced Persistent Threats
The evolution of UEFI Advanced Persistent Threats parallels the growth of the NSA and the Deep State. It started with the creation of UEFI in 2007. But it is still going on as can be seen by the March 2019 disclosure of Shadow Hammer – the latest NSA UEFI hacking tool. Below is a brief history of the UEFI Advanced Persistent Threats.
2007 NSA Launches Cyber War Against Iran called Olympic Games
The first public report on the NSA Cyber Warfare program was in a NY Times Jan 10 2009 article by David Sanger. The article stated that in the previous 15 months: “President Bush authorized new covert action intended to sabotage Iran’s suspected effort to develop nuclear weapons.”
https://www.nytimes.com/2009/01/11/washington/11iran.html?scp=1&sq=january%202009%20sanger%20bush%20natanz&st=cse
David Sanger then wrote a 2012 June NY Times article, and a 2012 book called Confront and Conceal, revealing that NSA and CIA officials met with President Bush in 2006 with a plan to launch a cyber warfare attack on Iran. This cyber warfare attack became known as Operation Olympic Games in January 2007 – the same month that UEFI version 2.1 was released with the SMM backdoor.
There were two versions of the Stuxnet virus – an early version which Kaspersky referred to as Fanny was launched in November 2007 - and a much more powerful version of Stuxnet was launched in early 2009 while Obama was President.
In February 2015, Kaspersky released a 44 page report on the Equation group – which we now know was the NSA- including about a dozen cyber weapons developed and used between 2007 to 2013. “There is one aspect of the EQUATION group’s attack technologies that exceeds anything we have ever seen before. This is the ability to infect the hard drive firmware.” https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2018/03/08064459/Equation_group_questions_and_answers.pdf
Can the existence of hidden code on UEFI be the reason that the file size of UEFI grew by a factor of 10 between 2006 to 2008? How else can these cyber weapons survive not only replacing the operating system, but even replacing the hard drive? According to Kaspersky, several other “Equation Group” cyber weapons date back to 2007 including a weapon called Duqu was compiled from a device running a Windows operating system on August 31, 2007.
https://securityaffairs.co/wordpress/1129/cyber-crime/stuxnet-duqu-and-the-sons-of-the-tilded-platform.html
2009 Stuxnet 2 is approved by Obama
Stuxnet began on December 24, 2008 with the registration of the domain name for one of its Command and Control servers. However, in January 2009 no wholesale destruction had been accomplished. Meeting with Mr. Obama in the White House days before his inauguration, Mr. Bush urged him to preserve Olympic Games. Mr. Obama took Mr. Bush’s advice.
The 2009 version of Stuxnet could not only be spread by USB but also by networks with the first infection of this new version occurring on June 23, 2009 according to Stuxnet log files uncovered later by Kaspersky. Just a few months earlier, in March 2009, researchers Alfredo Ortega and Anibal Sacco published details of a BIOS-level Windows rootkit that was able to survive disk replacement and operating system re-installation.
2010 The NSA Cyber War on Iran Escapes into the Wild – causing havoc all around the world
Despite spending billions of dollars on cyber warfare weapons aimed at the Siemans PLC systems used in Iran, the NSA was only able to slow down Iranian nuclear production by a couple of months. Iran was soon increasing production. But even worse, beginning in late 2009, Stuxnet, Flame and other NSA cyber weapons began to spread first to the Siemens PLC systems that controlled Iranian Oil Rigs and then to oil rigs all around the world. One of these oil rigs that used Siemens PLC systems was the Deep Water Horizon which begins to see drilling control computers crashing and Microsoft Blue Screens of Death in January 2010. On April 20, 2010, NSA hacking tools were partially responsible for the Deep Water Horizon Disaster. Total financial damage was more than $100 billion and the damage to the Gulf was beyond calculation.
According to the Deep Water Horizon Chief Electronics Technician Michael "Mike" Williams, five weeks before the April 20 explosion, in March 2010 he had been called to “check a computer system that monitored and controlled drilling.” Williams was in charge of all of the Deep Water Horizon’s computers.

In a sworn deposition from a hearing on July 23, 2010, Mr. Williams went into great detail describing the “persistent” problems the Windows computers on the doomed oil rig were having. You can download this entire report at the following link: http://techrights.org/wp-content/uploads/2010/10/deepwater_horizon_inquiry_7-23-10.pdf
On page 42 of the report, Mr. Williams states how long their computer problems had been going on: “For three to four months we’ve had problems with this computer simply locking up. We even coined a term, the blue screen of death, because it would just turn to a blue screen. You would have no data coming through …
Our sister rig, the NAUTILUS, was going through those growing pains kind of for us. We had already ordered all the equipment. We were just waiting on them to figure it all out so that we could copy their learning and make it work on our rig… Meanwhile, we were limping along with what we had. We had ordered new hard drives. They came in. We replaced the images on the hard drives for the software imaging, got them back running, the chair would run for two, three days, and they would crash again… The hard drives were replaced the week before the explosion. But the crashes kept occurring.”
It should be clear by now that what the NSA called “Persistence” that survives replacing the hard drive and replacing the operating system has deadly consequences for our entire planet.
2010 June Researchers “Discover” Stuxnet
On June 17, 2010, Sergey Ulasen was in his office in Belarus sifting through e-mail when a report caught his eye. A computer belonging to a customer in Iran was caught in a reboot loop — shutting down and restarting repeatedly despite efforts by operators to take control of it.
A total of five organizations in Iran were hit repeatedly in separate infections in June and July 2009 and again in March, April and May 2010. But due to the zero-day exploits in it, Stuxnet spread beyond these organizations, leaving a constellation of infections in its wake. https://www.wired.com/2011/07/how-digital-detectives-deciphered-stuxnet/
The security researchers notified Microsoft, but Microsoft did nothing to fix the security flaw. After 2 weeks of waiting, on July 12, 2010, Sergey Ulasen posted an announcement about the security problem.
In July 2010 Siemens stated that they had assembled a team to deal with the problem. But instead, they also did nothing for several months.
On August 6, 2010, Symantec published a post saying that Stuxnet was a targeted attack aimed at hijacking the Programmable Logic Controller in a Siemens control system by injecting malicious code. Each time Stuxnet infected a system, it “phoned home” to one of two domains — www.mypremierfutbol.com and www.todaysfutbol.com — to report information about the infected machines. The command-and-control servers let the attackers update Stuxnet on infected machines with new functionality or even install more malicious files on systems intended to sabotage the PLCs. Within a week of establishing the sinkhole, about 38,000 infected machines were reporting in from dozens of countries. Before long, the number would surpass 100,000. https://www.symantec.com/connect/blogs/stuxnet-introduces-first-known-rootkit-scada-devices
2010 August It fell to Michael J. Morell, the deputy director of the C.I.A. — to break the news to Mr. Obama. At a White House meeting, after being told that Stuxnet had escaped into the wild, Obama asked “Should we shut this thing down?” He decided to continue the attacks.
2010 September 23 Kaspersky issued their first report on Stuxnet calling it the world’s first cyber warfare weapon. https://www.kaspersky.com/about/press-releases/2010_kaspersky-lab-provides-its-insights-on-stuxnet-worm
2010 October Microsoft released a record number of patches aimed at countering the Stuxnet "worm" attacking industrial networks.
2010 November F Secure publishes first detailed analysis of Stuxnet noting that the start date for one version was January 2009 but was not discovered by researchers until June 2010. https://www.f-secure.com/weblog/archives/00002040.html
2011 October The Laboratory of Cryptography and System Security discovered an NSA weapon called Duqu. They issued a 60 page report comparing Duqu to Stuxnet. They noted that both Stuxnet and Duqu used valid digital certificates to bypass Microsoft security. The Duqu certificate was issued on August 3 2009. These are the only two viruses thus far to have valid digital certificates. While Stuxnet is 1.2 MB, Duqu is only 0.4 MB. Both cyber weapons use the same Dynamically Linked Library (DLL) functions. Duqu files date from April 14 2008. Both viruses have the ability to remotely update themselves from NSA Command and Control servers. The Duqu infection method uses a Microsoft Word document with hacking code hidden in the type face. Duqu hides malware in a JPEG image. https://www.crysys.hu/publications/files/bencsathPBF11duqu.pdf
December 28 2011 Cory Doctorow The War Against Your Personal Computer
“Our computers are becoming some combination of rootkits and spyware...Manipulated by traitors and spies working for criminals and control freaks... This is the opposite of computer freedom. This is computer slavery.”
In May 2012 Kaspersky released a report on the Flame Virus linking it to Stuxnet and Duqu
Flame had been created by the summer of 2008. Flame is a sophisticated attack toolkit, which is a lot more complex than Duqu or Stuxnet. Flame uses the Windows Automatic Update system to infect computers. It is a backdoor allowing it to replicate in a local network and on removable media if it is commanded so by its master. Flame can easily spread to other systems over a local network or via memory stick. Is able to record audio- through Skype or MSN, can take screenshots, is sensible on a keyboard activity. Basically is collecting the information and then sends it on a command station.
The Flame malware is a huge package of modules comprising almost 20 MB in size. A network of 80 Command and Control servers across Asia, Europe and North America has been used to access the infected machines remotely. Flame used a counterfeit Microsoft security certificates to verify its trustworthiness. Faking credentials from Microsoft would give the malware far more credibility than using certificates from other vendors, as would hiding updates in Windows Update.
https://www.f-secure.com/weblog/archives/00002377.html
Flame used two certificates issued by Microsoft Root Authority and one by Microsoft Root Certificate Authority. One of these certificates does not expire until 2016 and another does not expire until 2017. Thus, these certificates were valid for 5 to 6 years when the average certificate does not last for more than one year. This indicates that Microsoft may have worked with the NSA in issuing these very special certificates.
Here is what both Flame and Stuxnet did. First, they would attempt to connect to two valid websites to establish an internet connection. These sites were windowsupdate.com and msn.com. They would then connect to the malicious site futbol.com.
In September 2012, security researchers discovered security shortcomings in UEFI that create a means to infect the Windows operating system with rootkit malware. Italian security consultants ITSEC discovered the security hole following an analysis of the Unified Extensible Firmware Interface (UEFI). Mark Giuliani, the Director of ITSEC told El Reg. “Writing a rootkit couldn't be an easier task for virus writers with the UEFI framework available, much easier than before with BIOS when they needed to code in pure assembly. Marco Giuliani, Director of ITSEC, Hacking UEFI... New Vicious UEFI rootkit vulnerability found for Windows 8
https://www.theregister.co.uk/2012/09/19/win8_rootkit/
Linus Torvalds, the founder of the Linux project is also not impressed with UEFI. “The real problem, I feel, is that clever hackers will bypass the whole (UEFI) key issue either by getting a key of their own (how many of those private keys have stayed really private again? Oh, that’s right, pretty much none of them) or they’ll just take advantage of security bugs in signed software to bypass it without a key at all.” Linus Torvalds on Windows UEFI June 10, 2012
2012 August Kaspersky releases 50 page report on Gauss linking it to Flame, Stuxnet, and Duqu
https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2018/03/20134940/kaspersky-lab-gauss.pdf
While many domains are now hosted overseas, many were previously hosted on US servers. Flame uses more than 100 domains and more than 20 fake identities. Registration dates go back to January 2011 but code dates in Flame go all the way back to 2007. Gauss has encrypted its payload making it harder to analyze.
October 2012 With the release of Windows 8, Microsoft's certification requirements now require that computers include firmware that implements the UEFI specification.
2013 June Edward Snowden released one million NSA documents confirming that the NSA spends $52 billion per year on offensive cyber weapons. TAO changed its name to Computer Network Operations. At 10,000 paid hackers per billion dollars, this implies that the NSA has more than 100,000 “fusion agents.”
2013 September I published Free Yourself From Microsoft and the NSA summarizing UEFI problems and the connection between MS and the NSA. To get a free copy of this book, visit this link:
https://freeyourselffrommicrosoftandthensa.org/
June 11, 2015 Universal UEFI hacking tool released
A research report developed a system for hacking millions of Windows computers. See How Many Million BIOSes Would You Like to Infect http://legbacore.com/Research_files/HowManyMillionBIOSesWouldYouLikeToInfect_Whitepaper_v1.pdf
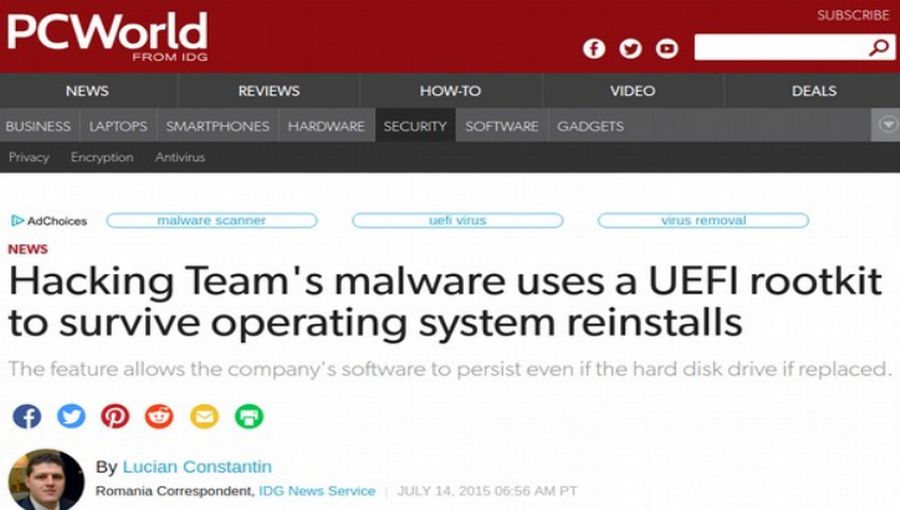
2015 July Spyware Firm Hacking Team was hacked exposing 400GB of hacking tools including a UEFI rootkit called Galileo.
Hacking Team charged more than 35 repressive governments a total of more than 40 million dollars to help their dictators spy on and arrest political opponents using the UEFI backdoor. The UEFI hacks had been used since at least 2012. https://blog.trendmicro.com/trendlabs-security-intelligence/hacking-team-uses-uefi-bios-rootkit-to-keep-rcs-9-agent-in-target-systems/
The UEFI malware made sure that Windows was always infected. If you’re a target of a Hacking Team customer, even formatting your disk and re-installing Windows would not remove the malware. As soon as you reboot, the malicious BIOS firmware would re-infect the freshly installed Windows with the same malware again.
June 2016 Microsoft Hands Golden Key over to Hackers
As if the insanity of handing the keys to our computers over to Microsoft was not bad enough, in June 2016, two computer security researchers discovered that Microsoft was doing some rather reckless things with these Golden Keys. Microsoft developers wanted to make changes to certain devices without going through the hassle of getting authorized keys to Secure Boot. So they developed a secret “super policy” for bypassing Secure Boot completely. Had this Golden Key “super policy” been discovered by hackers it would have given them unlimited access to nearly every computer in the world. This backdoor nuclear weapon was discovered by “Good Guy” researchers before it was discovered by Bad Guy hackers. https://www.infoworld.com/article/3106079/security/secure-boot-proves-insecurity-of-backdoors.html
After the researchers notified Microsoft of the issue, the company released a security patch MS16-094 in July 2016.
However, the July patch was not a complete fix. The issue remains only partially addressed. Even worse, it is believed it is impossible for Microsoft to fully revoke the leaked Golden Key Super policy.

Because of the implications of this Golden Key Backdoor being released to the wild, the two researchers wrote a letter to the FBI explaining why the entire concept of having super keys to all computers was a bad idea:
“Microsoft implemented a 'secure golden key' system. And the golden keys got released by Microsoft's own stupidity. This is a perfect real-world example about why your idea of backdooring systems with a 'golden key' is very bad!”
The first lesson we should learn from the 2016 Golden Key incident is that keys and secrets will eventually get leaked or stolen. The second lesson is that a fix is not always possible.
If we really want to protect our computers, we need to only use computers that do not use UEFI, Secure Boot and Golden Keys in the first place.
October 31 2016 Shadow Brokers publishes a list of servers in 49 countries that had been hacked by the NSA.
The list contained 306 domain names and 352 IP addresses that the NSA/CIA used as Command and Control Servers.
https://thehackernews.com/2016/10/nsa-shadow-brokers-hacking.html
January 10, 2017 I publish an 87 page report called Hack Everything exposing the NSA Role in the Hacking of the 2016 US Election

My report included analysis of 800 IP addresses supplied by the NSA in December 2016 as “proof” that the Russians hacked the 2016 US Election. I showed that all of these IP addresses fell into one of three categories:
#1: Public IP addresses (such as libraries and schools) in countries around the world
#2: TOR exit nodes being attacked by the NSA
#3: Fake Hosting Companies run as shell corporations by the NSA often pretending to be in foreign countries but in fact being registered as corporations here in the US. https://turningpointnews.org/phocadownload/Hack%20EverythingA%20Detailed%20Timeline%20of%20the%20DNC%20Hack.pdf
2017 March 7 Wikileaks releases Vault 7 exposing 8,700 CIA – NSA hacking tools. These Vault 7 hacking tools were made with 700 million lines of code times an estimated cost of $100 per line equals $70 billion dollars in tax payer funds paid for hacking costs – just for the NSA hacking software. Among the 8,700 NSA/CIA tools were UEFI hacking tools.

April 2017 UEFI Ransomware Video
https://www.youtube.com/watch?v=xYrcaa1fSXA&t=130s
Here is what your screen looks like at the end of this 5 minute video:

At the BlackHat Asia 2017 security conference, researchers from cyber-security firm Cylance disclosed two more vulnerabilities which allow an attacker to write malicious content to the UEFI firmware. They installed a UEFI ransomware, preventing the devices from booting. They noted the same flaws can be used to plant rootkits that allow attackers to persist malware for years. An attacker can exploit both flaws to execute code in the System Management Mode (SMM) and plant malicious code in the firmware itself. A vulnerable SMI handler allows the attacker to execute code in SMM mode where he finally can bypass any write protection mechanisms and install a backdoor into the system's firmware.
2017 April 14 Shadow Brokers released 300 MB of NSA TAO hacking tools including the Eternal Blue “point and click” remote controlled backdoor (later used in the WannaCry Ransomware attack as well as the Not Petya and Bad Rabbit attacks. "It is by far the most powerful cache of exploits ever released," Matthew Hickey, a security expert and co-founder of Hacker House, told Ars. "It is very significant as it effectively puts cyber weapons in the hands of anyone who downloads it."
2017 May Wanna Cry Ransomware attack strikes Windows computers and networks around the world using Eternal Blue causing about $6 billion in damage.
2017 October Intel announces they will remove the Compatibility Support Module (CSM) from UEFI eliminating Legacy BIOS as a firmware option in January 2020.
April 2018 20 Year Old Hacker Shows How to Hack UEFI
In this video a 20 year old hacker explains how to hack UEFI in 13 minutes. “You do not need to know much “Because UEFI is badly written software. I call this the Lord of the Rings attack Others call it the SMM attack. SMM is controlling everything “
https://www.youtube.com/watch?v=lzZvL1wZ-WM

2018 October video of 4 minute Evil Maid SMM UEFI direct attack at DEFCON 26 in Las Vegas using the UEFI update system. Remote 10 second Demo at 38 minutes in the video. “This is what Hacking Team did with their UEFI implant.”
The DEFCON hackers warned ASUS in 2018 and were ignored. https://www.youtube.com/watch?v=CxqNgjMZAbk
March 25 2019 Kaspersky exposes Shadow Hammer which has infiltrated the UEFI Update Systems of ASUS and affecting hundreds of thousands of computers. Security vendor Avira said it had observed at least 438,000 ASUS devices on which the initial malware installer was executed. ASUS has sold more than 4 million laptops in the past year that could now be infected. https://securelist.com/operation-shadowhammer/89992/
As with Not Petya, CCleaner and Flame, Shadow hammer is installed using a hacked vendor update. But instead of being an application update (Not Petya and Ccleaner in 2017) or an operating system update (Flame in 2012), Shadow Hammer is delivered using a UEFI BIOS update – making Shadow Hammer much more dangerous than either Not Petya or Flame.
The ASUS live update tool that delivered malware to customers last year is installed at the factory on ASUS laptops and other devices. When users enable it, the tool contacts the ASUS update server periodically to see if any firmware or other software updates are available. The malware reached out to asushotfix.com, a site masquerading as a legitimate ASUS site, to fetch a second-stage backdoor that it downloaded to that system. T
The attackers used two different ASUS digital certificates to sign their malware. ASUS has still not invalidated the two compromised certificates, which means the attackers or anyone else with access to the unexpired certificate could still sign malicious files with it, and machines would view those files as legitimate ASUS files. Furthermore, according to the reporter who broke the story, ASUS had also tried to have Kaspersky sign a non-disclosure agreement (NDA) in an attempt to keep the incident quiet.

Kaspersky researchers believe the Shadow Hammer attackers were behind the Shadow Pad and CCleaner attacks and obtained access to the ASUS servers through these attacks. Targeted MAC addresses of the Shadow Hammer attack includes VMWare and Huawei.
April 23 2019 Shadow Hammer New Details
We are dealing with a case of compromised digital signatures. The same two certificates have been used in the past to sign at least 3000 legitimate ASUS files which makes it very hard to revoke these certificates. Therefore, we recommend software vendors introduce another procedure into their software production process that additionally checks their software for potential malware injections even after the code is digitally signed.
https://securelist.com/operation-shadowhammer-a-high-profile-supply-chain-attack/90380/
Kaspersky extracted the history of changes and collected the following information indicating the time and C2C of ongoing operations in 2018.
The most recent Command and Control server for Shadow Hammer as of December 2018 has the IP addresses 23.236.77[.]175 and 23.236.77[.]177. owned by the Chinese hosting company Aoyouhost LLC,incorporated in Los Angeles, CA. The registration of this LLC was October 2013. While they have offices in Hong Kong, they have servers in the US. They have a lot of servers. This is their web page: aoyouhost.com
This is a very nicely coded bootstrap website. But why would a Chinese server company use images of Americans?
The website claimed that the hosting company started in 2010 - but the Wayback Machine indicates that their website did not go online until February 2013. Even stranger, in February 2013, the website looked almost exactly the way it looks today. No change in 6 years!
While most web hosts have as many as 1000 websites on a single server, auyouhost.com hosts only 85 websites all on US servers. Many sites hosted on this server appear to be very unusual. For example, Boiler-tubes.com is not really a website at all. Instead, the very unusual source code for this one page website is written in PHP and appears to be some sort of Database request.
Linux BIOS Options
Currently, if you want to buy a new computer that does not have UEFI, your only options are to buy a Chromebook (which uses Coreboot) and reflash it (see Learn Linux and LibreOffice dot org for more information on this process) – or buy a Purism laptop which also uses Coreboot.
2019 February Purism Announces Pure Boot Coreboot Laptops
https://puri.sm/posts/pureboot-the-high-security-boot-process/
PureBoot starts by loading a free software BIOS, coreboot, so that you can audit your BIOS for security bugs or back doors.
Linux Boot – Our Best Hope for a Secure Linux BIOS
What about those who do not have a Purism laptop? We need a BIOS that will work on any laptop… Ron Minnich is working on Linux Boot - a secure BIOS that uses the core of the Linux operating system as firmware. https://www.linuxboot.org/
October 27 2017 38 minute video by Ron Minnich about how we can replace UEFI with Linux Boot:

https://www.youtube.com/watch?v=iffTJ1vPCSo1
Replace Your Exploit-Ridden Firmware with Linux - With the WikiLeaks release of the Vault 7 material, the security of the UEFI (Unified Extensible Firmware Interface) firmware used in most PCs and laptops is once again a concern. UEFI is a proprietary and closed-source operating system, with a code base almost as large as the Linux kernel, that runs when the system is powered on and continues to run after your computer boots the Operating System. UEFI is therefore a great place to hide exploits, since it never stops running, and these exploits are undetectable by kernels and programs. Our answer to UEFI is NERF (Non-Extensible Reduced Firmware), an open source software system to replace almost all of UEFI firmware with a tiny Linux kernel combined with the u-root project (http://u-root.tk/)
The problem, Minnich said, is that Linux has lost its control of the hardware. Today there are at least two and a half kernels between Linux and the hardware. Those kernels are proprietary and exploit friendly. Worse yet, exploits can be written into the flash of the system so that they persist and are difficult or impossible to remove.
In 2018, Purism developed their own version of Coreboot for their Purism Linux computers. As Purism discovered, laptop makers can choose to have their hardware boot without looking for a digital firmware signature at all. The fusing of the processors can be set by the motherboard manufacturer to simply bypass the check. Purism's Librem 14 laptop ships with their version of Coreboot.

Recent Intel Myths
As resistance has grown to the UEFI monopoly, Intel has launched a sort of public relations (propaganda) campaign in an effort to convince us that the UEFI monopoly is somehow good for us. Here are some of the more recent Intel myths about UEFI:
#1 UEFI is not really a Microsoft or Intel monopoly. Instead UEFI is a friendly sort of non-profit “forum” allowing a bunch of Independent BIOS vendors to work together to standardize the BIOS. The fact that they all got together at the exact time in 2007 when the NSA was forming their PRISM partnerships is a mere coincidence. And of course, the increase in the file size by a factor of ten during the same year is also a mere coincidence. Standardization does not make our lives better. It simply makes it easier for the NSA to hack all of our computers. The idea that UEFI is merely a high tech community project borders on the absurd.
#2 Tianocore is the open source version of UEFI. This is also deeply deceptive. In fact, Tianocore is a version of UEFI which can be added to Coreboot but a lot of the code in Tianocore is not open source and will likely never been open source. Like UEFI, TianoCore is loaded with holes. The latest attack was disclosed on March 14, 2019. https://support.lenovo.com/us/en/solutions/len-22660
#3 Intel would like UEFI to be open source – and release the entire code to public inspection – but their independent BIOS vendor partners won’t let them. Actually, if Intel was really supportive of open source, then they should release the source code for the Intel Management Engine.
#4 UEFI is just a “specification.” This is like saying that Linux is just a specification or Windows is just a specification or that the Legacy BIOS was just a specification or the plans to the first nuclear bomb was a specification. When you blow up BIOS to be 10 times bigger than what is was just a year earlier, you owe the public a real explanation for what is in the 90% of the millions of lines of code that had not been needed the year before.
#5 UEFI has to be big because modern computers have a lot of firmware. While modern computers do have a lot of firmware, there was no increase in the amount and type of firmware between 2006 to 2008 when the code for UEFI exploded. The prior BIOS worked well with a small file size. Coreboot also works well for a small file size. So the claim that UEFI has to have 500 models with 100 connected to SMM is ridiculous.
#6 The ability to do Automatic Online Firmware Updates is important in case we discover a serious flaw in UEFI. In fact, the Automatic Online Firmware Update backdoor is the serious flaw in UEFI! How UEFI does its automatic updates is by leaving a few connections open between UEFI and the operating system (called UEFI run time services). These connections are an extremely bad idea because they allows hackers to move back and forth between UEFI and the operating system. Once hackers have access to either, they have access to both. Because the hardware does not change once the computer is made, there is no need for remote updates and remote updates can and should be avoided.
#7 UEFI has a lot of cool features. The problem with this claim is that we do not want or need the firmware initializer to have cool features. We simply want it to do what legacy BIOS did. Check the hardware and turn the system over to the boot loader. Anything else just creates a larger attack surface for hackers.
#8 We have to end support for Legacy BIOS because it is “old code” that is not as secure as the new UEFI code. In fact, just the opposite is true. The old code is a much smaller attack surface with no backdoor connection to the operating system. It is therefore much more secure than the new UEFI code.
Conclusion… How do we get a secure Linux BIOS?
We as a community need to develop and recognize some basic principles that will help us all recognize the difference between computer security and insecurity. Let’s look at what current computer insecurity looks like and use it to help us clarify some “security rules”:
What Deliberate Computer Insecure Looks Like
“Security holes (many intentional) the size of the Grand Canyon! Visit the wrong web site and your hard drive is re-formatted and your operating system is compromised.”
1 Code Encryption instead of open source code means that the code can not be independently inspected – easier to hide back doors and malware.
Security Rule 1: Safety requires open source code transparency. No transparency leads to hidden back doors and means no safety.
2. Monopolies such as Microsoft, Intel and UEFI mean lack of choice and single points of failure. They can not be trusted.
Rule 2: Safety comes from diversity. There is a benefit to having many Linux operating systems because it makes it harder to attack.
3. Remote Controlled versus User Controlled Changes. Top Down Remote Controlled changes are automatic back doors for hackers. Using top down keys digital certificates (aka keys) driven by monopolies to mandate remote controlled changes to the software – changes that are not under the users control.
Rule 3: Safety requires bottom up user control. Top down control means no safety means single points of failure. Top down certificates do not work. If certificates are used, they need to be generated and controlled from the bottom up by local users. Avoid Centralization. Avoid Top Down.
4. Placement of the web browser inside of the operating system leads to an obvious back door for hackers. Windows is the only OS that placed a web browser in its core. Bill Gates did this over the strong objections of many Windows programmers. There should be no web browsers in the Processing Unit or the BIOS.
Rule 4: Security requires that applications should not be able to “call home” without the users permission. There should not be call home functions in processors (no Intel Management Engine) or in BIOS firmware (no UEFI automatic updates).
5. Large and complex code structures that increase the file size for no apparent reason and thus increase the attack surface.
Microsoft merged web browser Internet Explorer inside the core of the Windows operating system over the objections of their own programmers. UEFI also presents a massive attack surface.
Rule 5: Safety comes from simplicity. There should be a reason for every line of code. There should not be hundreds of hidden modules inside of UEFI. If a system becomes infected, the system should be simple enough for the user to easily replace everything on the system and start over.
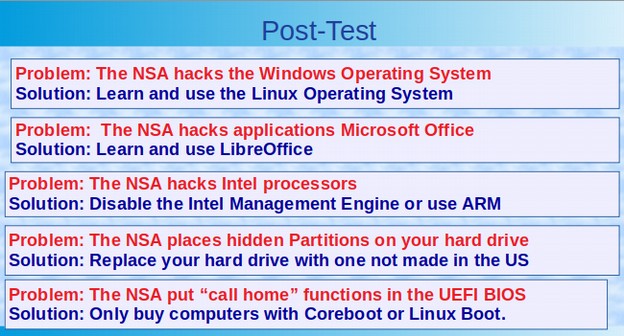
What’s Next?
Did I mention that Apple computers also require the UEFI remote control kill switch? The only way to avoid the UEFI remote control kill switch is to either buy an older Windows computer and turn off UEFI and then install Linux – or buy a Linux computer than does not come with UEFI. We will describe non-UEFI hardware options in Chapter 2.